What is consumer-permissioned data & how does it work?
While banks and aggregators have done an impressive job shaping conventions and standards around consumer-permissioned data, we think that's an incomplete solution. That's where we step in.
A look inside the world of data aggregators and consented API connections
Here at Portabl, we live at the intersection of identity and open banking. We are committed to transforming what it means to verify and reuse trusted identity.
Up until the last decade or so, consumers have had little control over their own information. While banks and aggregators have done an impressive job shaping conventions and standards around consumer-permissioned data, we think that's an incomplete solution.
Consumers want more control and transparency out of their data; businesses want stronger customer relationships, less friction, and better unit economics.
That's where we step in.
Portabl bridges the gap between simpler account access and secure data sharing.
We're building the infrastructure to prove consumer identity in seconds and ensure those verifications can be used, friction-free, downsteam by the consumer—2 clicks, zero passwords.
Inspired by the surge in advancements in cryptography, self-sovereign identity, identity wallets and next-gen privacy considerations here and abroad, we're making it as easy to reconfirm KYC, account and payment data with the ease of SSO—connect once, connect anywhere and update once, update anywhere.
This is our commitment to the future of consumer-controlled & reusable ID management.
But before jumping into the world of decentralized identity and our views on consumer-controlled data, let's walk you through the current state of consumer-permissioned data.
Key Highlights:
- What is consumer-permissioned data?
- Why is user-permissioned data important?
- How does consumer-permissioned data work today?
- Shortcomings
- How to get started with Portabl
What is Consumer-Permissioned Data?
Also known as user-permissioned data, consumer-permissioned data is an umbrella term for methods for some requesting party (a relying party) to access personal information quickly and securely without breaching privacy standards from one or more underlying sources.
For this connection to work, an individual/consumer gives consent and authorization for App A to consume underlying bank data via an aggregator or intermediary
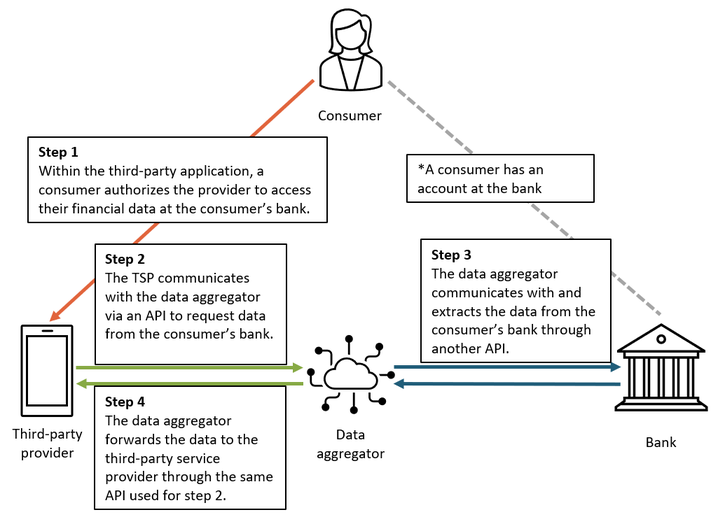
Historically, reliant parties accessed consumer financial data through “screen scraping.” In this process, a reliant party would log in to the consumer's bank account and extract data, often using a data aggregator to collect and package the data. In the past few years, screen scraping has (rightfully) come under fire due to its fragility and weak security posture.
Today, the vast majority of consumer-permissioned financial data moves from financial institutions to relying parties through application programming interfaces (APIs). While consumers still have the authenticate into their underlying account in order to authorize the connection, APIs-based methods of data sharing afford more granular control while financial institutions act as gatekeepers.
Common examples
- Connecting a bank account to an investing app to set up a method of funding transactions
- Applying for a credit card and connecting 1 or more payments accounts so that transaction information can be factored into the underwriting decision
Why is user-permissioned data important?
It's pretty clear that consumer-permissioned data has moved the open banking conversation forward in the US and abroad, and started closing the access gap between consumers and the diverse array of services available to them in the market.
The average American consumer has at least 5-7 financial accounts under their name and some have even more. Some customers have over 30 financial accounts across checkings, savings, credit cards, investments, loans, etc. And since 80% of Americans want to do business with their banks digitally anyway (according to a 2019 FDIC study), it's no surprise that consumer-permissioned data connections are at the forefront of digital financial growth.
Where are consumer-permissioned data experiences coming up short?
However, the status quo is not as rosy as it appears.
- Connections break
- Authentication steps—worse, redirects—are still a source of friction and dropoff
- The "verify from scratch" problem is not solved for specific use cases, making onboarding costs higher than they ought to be
- Concentration of connectivity among a few providers creates pricing risk
- Despite the consumer-permissioning baked into these interactions, there's a lot that's left hidden from the user, e.g. revoking authorizations, how data is stored, whether connections are persisted after account closure, etc.
- User data fragmentation is rampant—users are burned with managing connected accounts, permissions, and privacy setting across every downstream app and provider they use without any sort of "headquarters" that has both read and write capabilities.
How we're solving this at Portabl
By building the standards for reusable financial ID, we're moving the industry from consumer-permissioned data to consumer-controlled data.
Passwordless auth & bank validation, reusable KYC and and continuous identity—these are some of the most important ingredients that go into building the best financial and ID management platform out there.

Reusable KYC & bank-verified info
We're kicking repeat verification to the curb by offering reusable KYC to users and an onboarding experience based on trust, transparency and simplicity — identity and bank information in a single set of sharable information without a redirect or additional log in process. This speeds up the onboarding process for consumers and shrinks the costs and attrition rate during the activation process.
Strong Passwordless Authentication
Our system is designed to stop ATOs and phishing attempts with a strong passwordless authentication supplemented with a first-to-market method for reciprocal authentication. This two-way authentication requires businesses and users to verify themselves before any data sharing event occurs.
Continuous Identity
We want you to be able to verify that your users are who they say they are in real time with real-time updates. Continuous identity allows businesses to securely subscribe to their users' verified updates and drive automated coverage across multiple platforms. On the other end, consumers can build and manage a portfolio of their accounts with first-in-market capabilities around update once, update everywhere
The effects?
- Increased conversion rate
- Stronger data security*
- Enhanced controls over privacy and consent capture
- Real-time data, all the time
Consumer-controlled vs. consumer-permissioned?
We'll be back next week with a deep dive into how our platform reimagines what it means to share standardized data in real time in ways that are cheaper, more secure, and more delightful than the status quo.
If you've started asking yourself what the difference is between federated identity and decentralized identity, then this next article is for you.
Meanwhile: How to get started with Portabl
Today's consumers are ready for the future of ID management. They are savvier than ever and understand the true value of their data and want to know how it's being used.
Portabl's platform empowers users to manage their own data and offers businesses the tools needed to ensure smoother conversions, enhanced privacy greater overall user value. If you're ready to learn more about the work we do, you can get started here.
