Hello 2024! Passkeys, consortium whitelisting, audit logs, ID diffs, and more
Starting the year with a bang: say hello to Passkeys, build-your-own consortum, and a new and improved audit log.
Hello and happy new year! We’re excited to dive right in and share some new feature announcements!
🔑 Passkeys — single step authentication & onboarding
We’re thrilled to announce that Passkey-first verification is out in the wild, making document- and bank-based ID verification and onboarding as simple as FaceID or TouchID.
By introducing Passkeys as a preferred authentication factor, business now have 1-click biometric-based access to verified identity attributes, documents, and bank-validated data all via API and SDK without having to make expensive calls to underlying sources or the originator of prior verifications.
We already combine strong, passwordless authentication with reusable KYC to simplify onboarding, increase conversion, and minimize friction along the way with a verified ID that’s transferrable across apps and providers.
Passkeys for iOS and Android are multi-device by default, making access simpler and safer across web, mobile web, and native app. End users can set up passkeys at any time through their Portabl Passport or through an embedded verification event in our network.
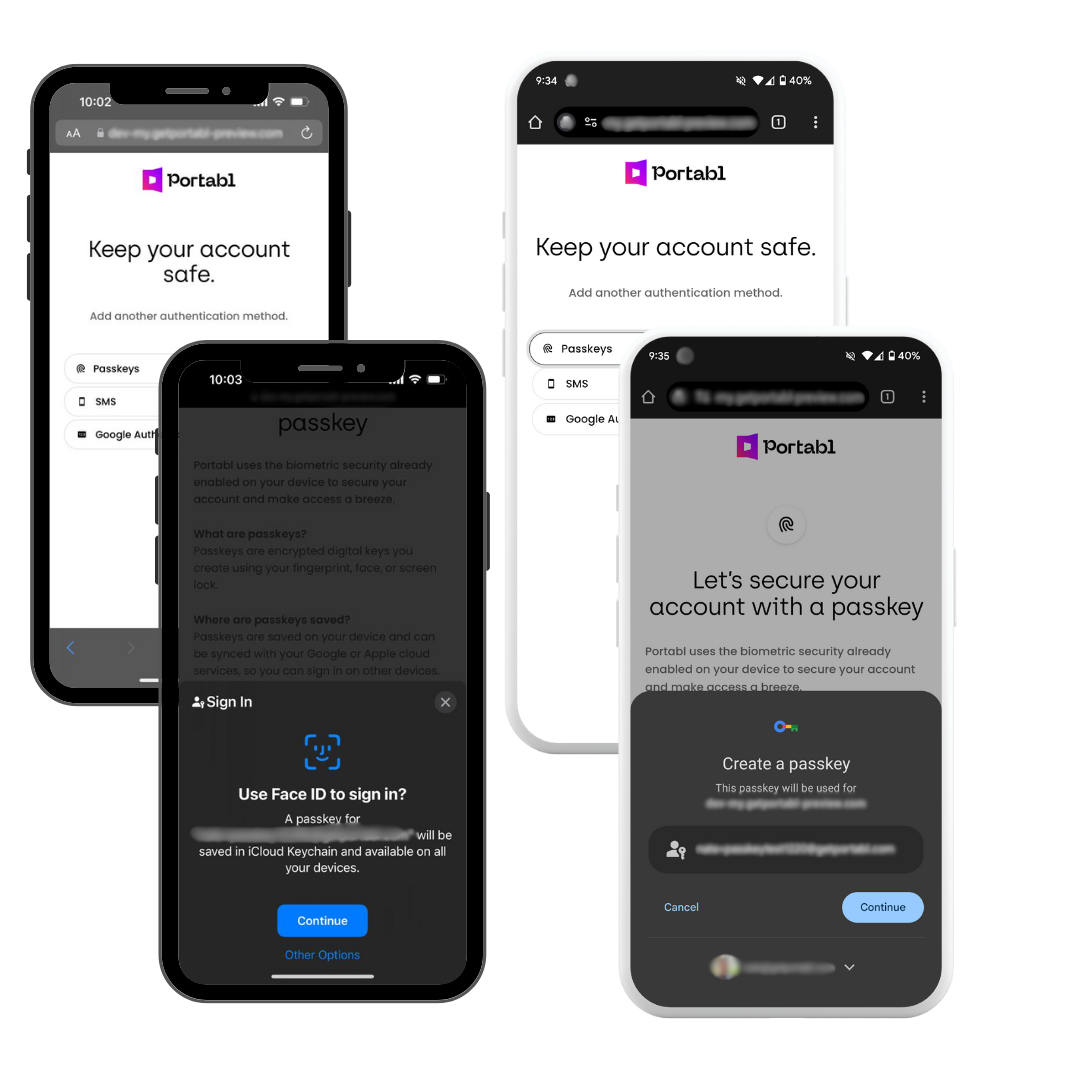
By combining the leading techniques in biometric auth with high-assurance data sharing via Verifiable Credentials, Portabl can shrink user registration across a spectrum of use cases to about 12 seconds and only a few API calls.
- 1 step biometric auth: Your first call will attempt to authenticate your user. While we still support traditional 2FA methods, e.g. email+otp, we see passkeys as the future for one-step authentication across a user’s financial landscape. A successful authentication event creates the ATO-proof bridge between end user and requesting party based on the DIDComm protocol.
- 1-step user-permissioned ID: Your second call will the verifiable credential process based on OIDC and W3C credential standards. Within seconds, your app or service will be able to prompt the user to re-share verified data or validate new data if not already associated with the user. This shrinks tedious data entry and collection down to a single user-permissioned event, where the underlying data maintains the source, provenance, and risk signal metadata needed to decision users and convert them.

User-side bindings power a spectrum of high-assurance outcomes
With this rollout, Portabl now cross-links (or “binds”) the device, ID documents, and bank-based information (and cryptographic keys) to the same real person, all without oversharing or overexposing data to relying parties on the other end. We do the heavy lifting of connecting the dots on the user-end, so only what’s strictly necessary is shared at the time it’s needed.
The practical effect is that behind each identity wallet there’s a high-fidelity, high-assurance identity attached to a real person, but businesses performing verification can dial up or down the scope of verification to handle anything from proof of personhood or residence through KYC based on docs, bank-verified ID, or a mix.
And as always, once a Portabl user is verified once in the network, a user can use that verification downstream to satisfy some or all of an additional verification process.

🤝 [2] Build a consortium via Trusted Issuers
We’re happy to release this one after a ton of feedback from platform providers that all boiled down to the same point:
“I have 100s of my own customers, and I want to build a network specifically inside my ecosystem to make ID reusability a benefit for them and the end users.”
Businesses in our network can whitelist their partners or affiliates in order to pare down the types of allowable credentials based on the underlying signer.
By restricting the reusability scope, approved—"known"—end users can now set up accounts at partners and affiliates in seconds. Businesses can push new-to-network users through pre-defined KYC steps in lieu of verifying an existing credential.
We take a private-by-default stance, so businesses looking to leverage this function need to opt into being discoverable by their partners and affiliates.

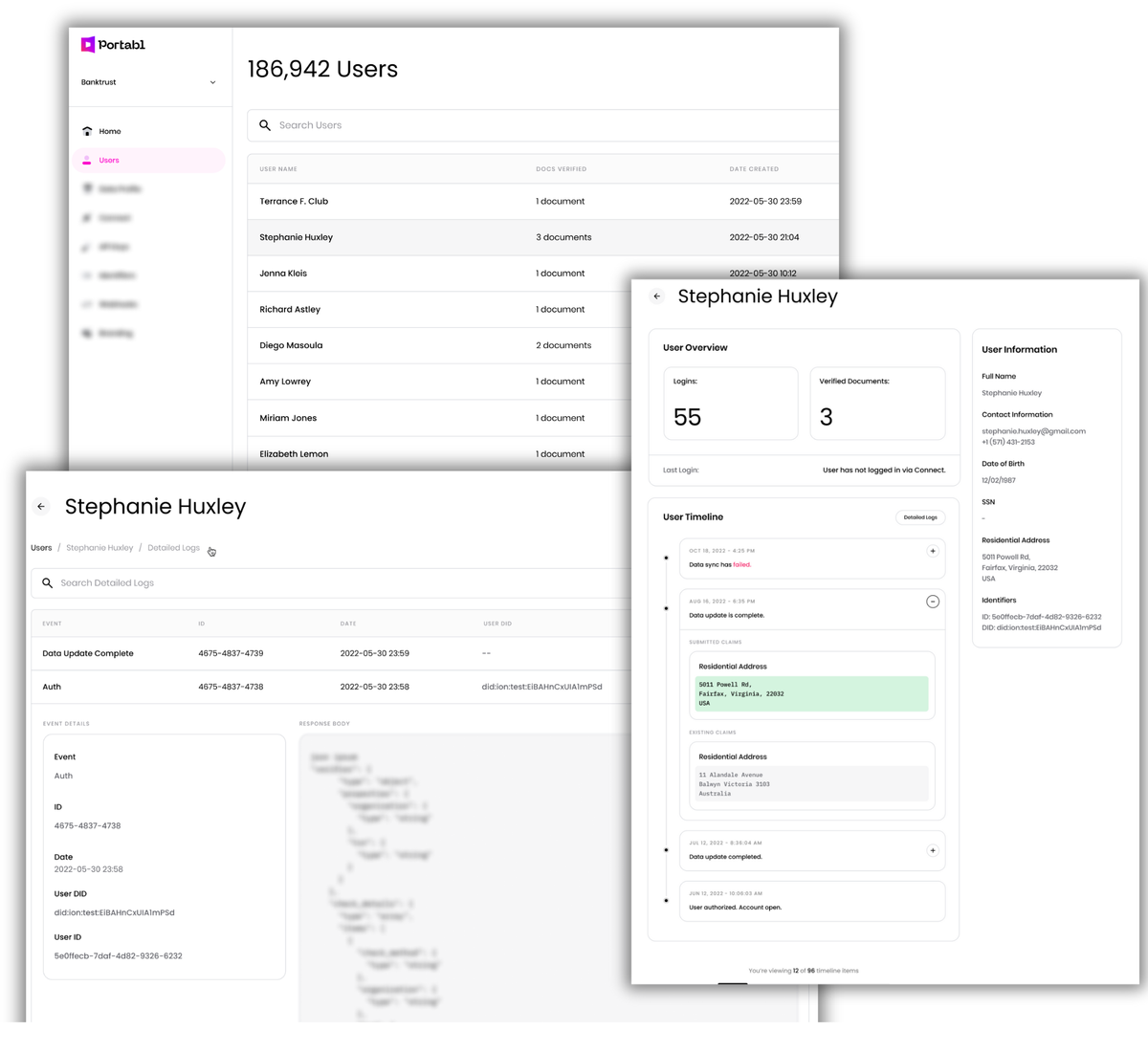
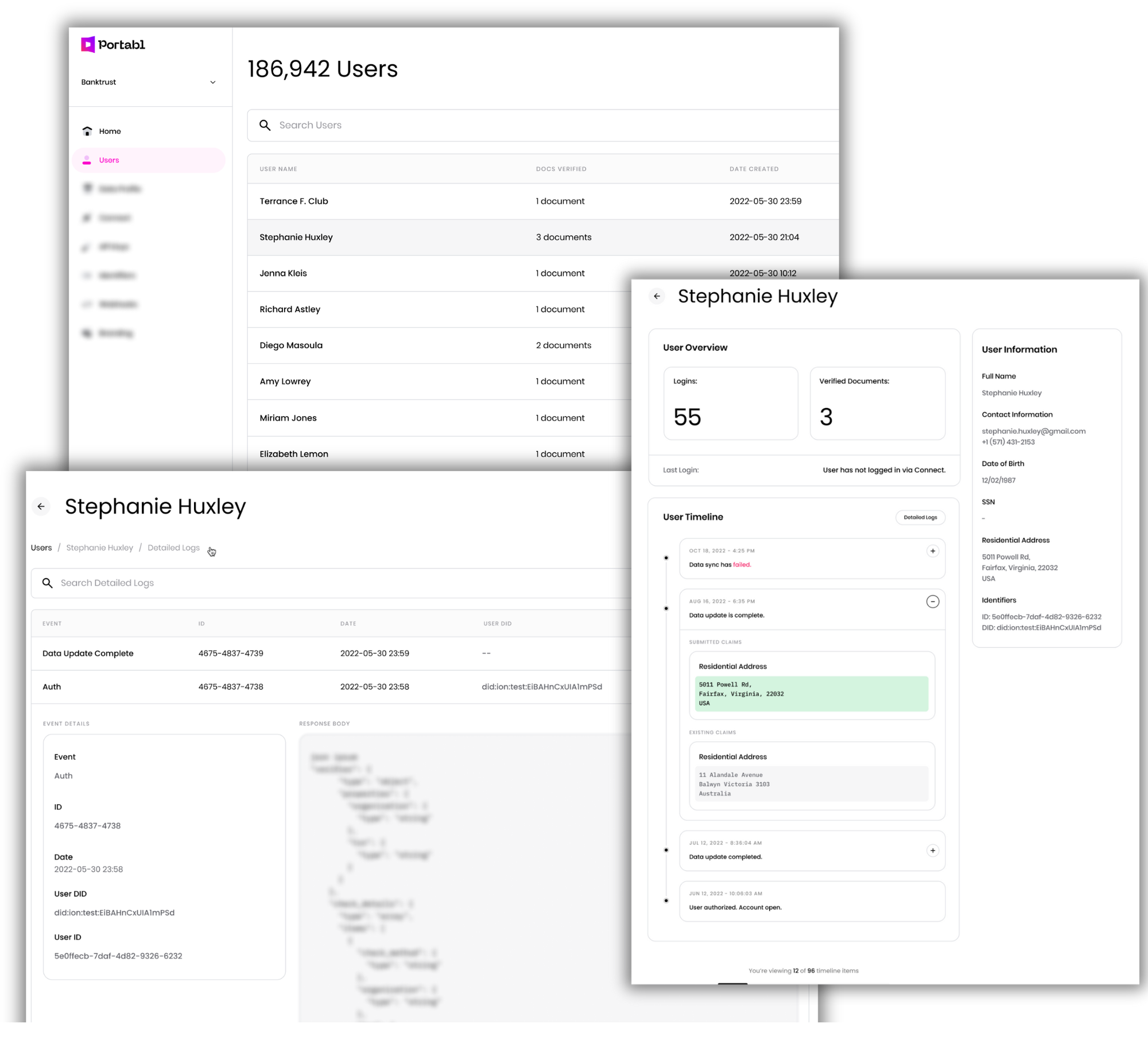
[3]User track changes and detailed logs
We built a brand-new set of interfaces around our system and audit logs in order to provide additional transparency and usability around system events, verifications, and data updates. Each end-user record is split into a timeline view and a detailed log.
The timeline view is akin to track changes, and surfaces key status changes as well as any data-level change performed in the native app or pushed from the Portabl Passport. As we build out more case management features, they’ll live here.
The log views provide raw output for both credential and authentication events, as well as granular process status updates and debugging information.
As we pick up steam in the new year, prepare for more announcements soon: tenant- and project-level configuration, multi-template support, dynamic fill, aggregated accounts in the user wallet, step-ups, and more.
